
Are Mobile Crypto Wallets Secure?
8 Jul 2023

8 Jul 2023
Many people use mobile wallets to store their cryptocurrencies, but how secure is a crypto wallet on your phone? Learn about the different types of mobile wallets and find out how they stack up when it comes to keeping your crypto assets safe.
A mobile crypto wallet is a software program that you can easily download on your mobile phone to store and use cryptocurrencies. Typically, mobile wallets are considered a type of “hot wallet”, meaning it is connected to the Internet using your mobile phone.
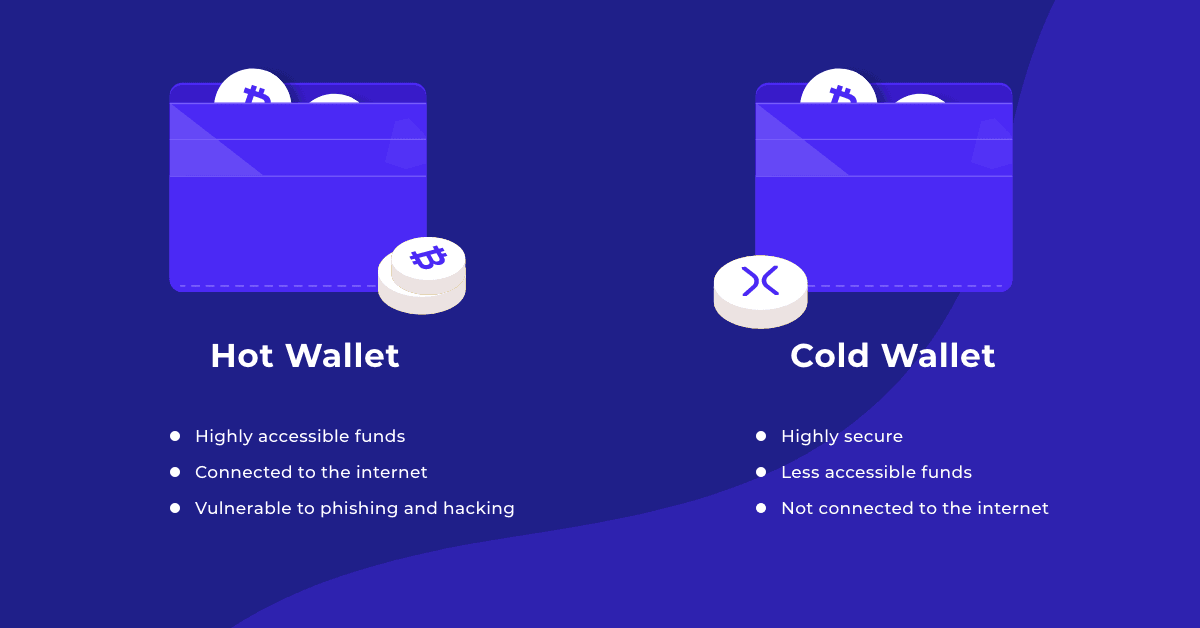
Hot wallets are very convenient to use but are more vulnerable to hacks. This is because there are more attack vectors when your crypto is stored online as opposed to offline. On the flip side, hot wallets provide more convenience and access to more crypto assets than cold wallets. Examples of mobile “hot wallets” include exchange wallets, browser wallets, and mobile wallets.
Source: Coingate
Cold wallets are software programs combined with an offline storage system, such as a hardware device (hardware wallet). Cold storage can also mean physically storing the seed phrase on a piece of paper (paper wallet). Some crypto users will even engrave their seed phase onto metal as a form of cold storage.
Using a cold wallet provides a higher level of security but is less convenient. To move crypto in or out of the cold wallet or make any transactions, users must connect the crypto assets in cold storage to an online device. Additionally, the wallet owner must safely store the hardware device or paper wallet, adding another layer of complexity.

Mobile wallets offer a high level of convenience while remaining more secure than traditional online or exchange wallets, which are always online and susceptible. The process for getting a mobile wallet is simple; it’s just downloading any app.
As an example, a mobile wallet that you download from the App Store or Google Play will act as the fastest and most convenient wallet for sending funds to an exchange account or NFT market.
But beware: Once you send crypto from your self-custody wallet to a centralized exchange or platform, you lose control over the private keys to your crypto assets.
With an increasing number of crypto scams and hacks in recent years, and several major crypto firms going bust in 2022, self-custody and maintaining sufficient wallet safety procedures have become more critical than ever. - Jesse Ellis, Blockchain.News
Many mobile wallets are self-custody wallets (or non-custodial). This means that the user controls the private keys, so they have control of their assets. But they also must personally ensure the safety of their crypto.
Exchange mobile wallets require you to give up control of the private keys. Essentially, the exchange owns the assets and if they were to go bankrupt or come under harsh regulatory action, you could lose access to your crypto in the blink of an eye.
On the other hand, exchange wallets often provide a higher level of security than an individual would have. Most have some form of institutional cold storage and insurance for their custodial assets.

Many mobile wallets do not have the same security features as desktop wallets, making them even easier for hackers to target. As a result, it is important to take some precautions when using a mobile crypto wallet.
When choosing the wallet for you, it is important to find one that is reputable and has a good security track record. Here are 5 strategies to try when shopping for a secure crypto wallet:
A new class of mobile wallets is hitting the industry with Gridlock leading the way. These ultra-secure wallets utilize distributed key generation and social verification to provide the highest level of protection for the crypto holder.
Distributed key generation means that the private keys to your crypto are distributed upon generation so that no one has access to the entire seed phrase, only key shares. If you lose your private keys or your device is compromised or damaged, the key can be recreated using a social verification network.
Social verification spreads out the verification process among several participants of your choosing. In the case of seed phrase recovery, a certain number of participants, called Guardians, is required to be online for the verification to take place. The same goes if you lose your device. Once you have your new device, your social verification network can easily help you regain control of your crypto assets.
In the early years of crypto wallets, users had to strike the right balance between convenience and security when choosing mobile wallets. Today, due to advanced blockchain and threshold signature technologies, crypto holders can enjoy both convenience and high security.
Suppose you are starting out in the world of cryptocurrency. In that case, it's never a bad idea to do a practice drill in case you ever have to recover your crypto in the event of a hack, scare, or broken device.
Spend an hour every few months to make sure you know how to restore your wallet. Since the birth of crypto, those who can protect their tokens have reaped the largest rewards, and with a little planning and a Gridlock Wallet, you can achieve this as well.
Experience crypto security like never before - Download Gridlock Wallet today!
- - -
Written by Mason Winsed

Mason Winsed simplifies blockchain for the people. With a comp-sci background and a passion for crypto safety, he's your go-to for straight-forward crypto wisdom. In his off time, he's coding or gaming. Join Mason for a no-nonsense crypto talk.