
What is Proof of Identity in Gridlock?
5 Mar 2024

5 Mar 2024
This post will provide insights into Gridlock's advanced security features, which safeguard your crypto assets through a decentralized guardian system, eliminating single failure points. You'll learn about the roles of Social and Institutional Guardians in transaction authentication, how to conduct transactions securely within Gridlock's network, and the technical foundations that make it possible. Additionally, you'll discover the benefits of Gridlock Watchtower and Lockdown features for enhanced security. This knowledge will equip you with the understanding needed to protect your crypto assets more effectively, highlighting Gridlock's advantages over traditional crypto wallets.
Gridlock delivers unparalleled security through a decentralized network of nodes that together protect your crypto assets. These guardians are essential for distributing crypto access, so there is never a single point of failure. They can also help you with distributed approval, which protects against one of the weakest parts of crypto ownership: the owner. It's an unfortunate truth that crypto ownership is difficult, and many losses can be attributed to personal mistakes. Gridlock solves this with a storage network where you are the owner, but the platform does all the work related to secure storage.
Gridlock's storage network consists of various types of guardians, including friends and family, called Social Guardians (SGs), and institutional guardians like the Gridlock Guardian (GG) and Partner Guardians (PGs).
Social guardians authenticate based on personal relationships, essentially using your personal connection as proof of identity. They know you and can contact you, if needed, to confirm that you are doing the right thing.
Institutional guardians (GG and PGs), on the other hand, utilize standard protocols when authenticating a user's identity. This typically involves sending an email (or other authentication methods like SMS, MFA, etc.), which you must confirm before the guardian approves an action. This step is a common practice in modern-day platforms that seek additional confirmation from a user before allowing access. Think of the extra steps you must perform when logging into an account from a different computer. Institutional guardians perform the same process. However, it's important to remember that Gridlock and its partner guardians do not have full control over the stored assets; they only manage their respective single keyshare.

A standard storage network has five devices, each holding a keyshare. These devices include one owned by the user, two owned by Gridlock Guardians (GGs), and the final two held each by two different Social Guardians (SGs). Users also have the option to expand their network beyond five guardians or use Partner Guardians (PGs) to expand the types and variety of storage devices that protect their network.
The owner's device is important because it is designated as the main device. Access to this device allows you to initiate transactions. The other guardians see this device as the primary driver because it uses a special keypair identifier to prove that it's the main device in the network. Once this device starts a transaction, the other nodes will automatically sign the transactions
This approach is similar to how basic crypto wallets work, such as MetaMask Wallet, Coinbase Wallet, or Trust Wallet. Whoever has access to the wallet can initiate transactions. This security consideration cannot be solved with basic wallets like Coinbase Wallet but can be solved with Gridlock. More on that later in this article.
While there are some considerations when putting transaction control into the hands of a single device, it's important to remember that Gridlock still offers huge benefits over the basic wallets that exist today simply due to the distributed nature of storage.
Gridlock protects against loss and theft since there is no single point of failure in the system. Splitting the key into keyshares means you're distributing the key to protect it from loss. Even if a couple of keyshares go missing, you haven't lost the whole key. Plus, getting back any lost keyshares is easy and fast—way simpler and safer than dealing with the headache of a single, all-important backup seed phrase that, if lost, means that all funds are gone forever.

An elevated transaction in Gridlock is a special action that needs extra approvals. This includes:
For any of these actions, Gridlock leans on other devices in the network to approve a transaction. This approach balances external security without forcing you to hand over control to a third party. It contrasts with centralized exchanges, where the exchange holds ultimate ownership and control of your crypto. Sometimes, it is beneficial for external oversight, which can help block suspicious transactions, but it is frustrating when it prevents legitimate ones. With Gridlock, you get the same protection, but control is decentralized, offering similar external oversight and protection while always keeping you in control.
Collecting approvals from devices in the network is generally fast and easy. Social Guardians (SGs) tap a button on their smartphone to approve the action. In contrast, enterprise guardians like Gridlock Guardians (GG) and Partner Guardians (PGs) use a wide range of authentication protocols.
These protocols have the speed and efficiency of standard auth practices you are familiar with, such as email confirmations, but add even more security than a single server-client relationship. Even if a hacker compromises one authentication tool, they still don't have enough control to steal your funds because they would first need to compromise multiple authentication methods used by the various enterprise guardians in your network.
Gridlock's architecture is centered around a cutting-edge cryptographic engine built in Rust. This engine performs the intricate cryptographic operations needed to securely sign transactions in a decentralized framework. Despite the advanced cryptography, the engine's design is fundamentally simple, with the sole purpose of transaction signing.
The crypto engine is surrounded by the main Gridlock app, which connects the user to the crypto engine and helps transmit signed transactions to the wider crypto ecosystem. The crypto engine provides security, while the surrounding application provides usability.
Below is the general processing of a transaction in the Gridlock system from the viewpoint of a Guardian device
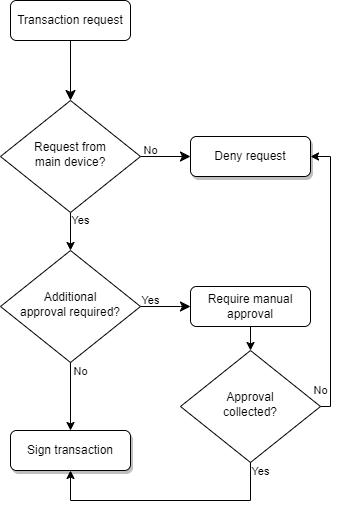
As mentioned above, there are many ways in which additional approval might be needed. The primary ways are predefined limits, suspicious transactions, and wallet lockdown.
It is important to remember that Gridlock operates on a fully decentralized system, meaning no single organization has control over assets or the approval process. Each guardian makes independent decisions on approving or denying transactions without influencing other network devices. Approval mechanisms differ between the different types of guardians.
For Social Guardians (SGs), approving a transaction is as straightforward as clicking a confirmation button. This simple step offers surprisingly strong protection against a common vulnerability in the crypto world: user error. Whether it's due to tiredness, distraction, or frustration, we've all made hasty decisions we later regret. This vulnerability is often exploited through social engineering, where hackers trick individuals into making mistakes.
Social Guardians serve as a defense against such tactics. When an SG is prompted to confirm a transaction, the network provides us with an additional opportunity to spot anything suspicious. This mechanism is not just about adding a layer of security; it's about giving our trusted guardians a moment to pause and review a transaction for our benefit.
Partner Guardians (PGs) use a more complex approval process based on the same authentication methods used by most internet companies, commonly referred to as two-factor (2FA) or multi-factor authentication (MFA).
You're likely familiar with this when you log into an account from a new device and need to verify your identity, perhaps through a confirmation email, entering a 2FA code, or answering security questions. Partner Guardians use this method to verify your identity before confirming a transaction.
PGs authenticate your identity in several ways, including:
In the future, we plan to implement decentralized ID (DID) support to improve the user authentication process further.
Getting approval from a Gridlock Gridlock (GG) mirrors the process used by Partner Guardians, highlighting our commitment to making crypto storage straightforward and non-custodial. We've designed Gridlock with the principle that we should never control your funds, ensuring that even in an unlikely scenario where we attempt malicious actions, the system is built to prevent any negative impact on your assets.
Let's explore how Gridlock is designed to prevent disruption, intentional or not. We are proud of what we've accomplished in our mission to create an easy, secure, and self-custodial platform.
Can Gridlock stop the transaction signing process? NO!
Gridlock uses a highly reliable and scalable messaging system called NATS for communication between guardian devices. Although Gridlock manages the primary NATS network, other partners operate additional networks independently. This decentralization means Gridlock cannot interfere with or halt communication between devices. Moreover, should the internet fail entirely, you can still access your private key using Gridlock's Eject feature with the aid of in-person guardians, ensuring your assets are always under your control.
Can Gridlock purposely cause problems by interfering with the distributed signing process? NO!
Imagine a scenario where Gridlock or any other guardian attempts to disrupt the system by signing transactions maliciously. This would simply result in the device being seen as "not signing" the transaction. As long as you have enough approving guardians in your network, you can complete a transaction, circumventing any devices that are lost, compromised, or act maliciously.
Can Gridlock stop the transmission of signed transactions to the blockchain? NO!
Once a transaction receives sufficient keyshare approvals, it becomes a fully signed transaction ready for the blockchain. At that point, any device with an internet connection can broadcast that transaction to the appropriate blockchain.

Gridlock Watchtower revolutionizes crypto asset ownership by merging the autonomy of self-custody with the security benefits of third-party oversight. This innovative feature ensures you benefit from the rigorous security and monitoring typical of modern financial systems, all while retaining absolute control over your assets. With Gridlock, you are the sole owner of your digital assets. No external party can control your assets, not even Gridlock. Traditionally, the burden of security in a self-custody scenario rested solely on your shoulders. Gridlock Watchtower fixes that by integrating third-party protection without compromising your control.
Imagine one day you stumble upon a deal that screams "too good to be true"—because it is. You're tempted to send crypto to an address promising tenfold returns. Even with seemingly convincing evidence, it's a risk. This is where Gridlock Watchtower shines by actively monitoring transactions to detect established threats and emerging scams in real-time.
If anything seems suspicious, Watchtower will flag the transaction, prompting approval from your guardians. This gives you the third-party protection you want, but you always have the ability and control to proceed with any transaction if you want. After all, it's YOUR crypto, no one else's.

Gridlock already stands out against even the most secure crypto wallets like Ledger or Trezor by offering a distributed storage network that is not vulnerable to any single point of failure. Now it's getting even better! Gridlock's Lockdown feature further elevates your security with multi-device approvals. It's an additional layer of security, allowing you to require multiple distributed approvals for a transaction. You get peace of mind knowing that your crypto cannot be sent away with a single, quick action.
This same multi-approve strategy is used in ultra-secure bank vaults and is now available to Gridlock Pro users. It works by designating a specific number of additional approvals from guardians that must be obtained before a transaction is signed. This ensures that that access to your primary device is not enough to steal your assets. Even if someone unauthorized is able to access your phone, they can't spend your crypto without approval from all the guardians you've selected. This is not possible with any other crypto wallet, where a bad actor could steal all of your funds if they have access to your wallet.
- - -
Written by Reid Zedkongor

Reid Zedkongor is peeling away layers of confusion around blockchain and cybersecurity. With a computer engineering background, he can dive into the details of crypto complexities to make crypto adoption easy for everyone. In his free time, he often reads fiction or enjoys a good laugh over a beer.